When I was looking at setting up my Plex Media Server, the one thing that I really wanted to make sure was that I kept the entire setup simple. I wanted to set up and manage a server that could stream media files to my devices, and not much beyond that idea. This meant I didn’t need a high-end and powerful computer to accomplish the goal, but I did have to make sure the system could handle at least three media transcoding operations at a time.
Once I had settled on the server, installed the operating system (Windows 10 Pro) the next thing I did was to decide how I wanted to set up my Plex media files. I also had some other services running on my desktop that I figured I could have my server manage, such as my regular data file management and backup. At this point I decided to look at how best to use the server to manage as much of my files as possible, while at the same time automating as many processes as possible.
I began to think about some ideas.
My Plex Media Server Ideas
I was running the Plex media server from my main desktop for a year before investing in the dedicated server. All my Plex media files were stored on a Western Digital Duo 8TB external drives connected to my desktop through USB 3.0, which I wanted to keep as is.
The Western Digital Duo external connection does contain to Western Digital Red drives, and one drive was a mirror of the other. For the mirroring, I wanted this to be more automatic, but without the use of RAID 1. On top of the automatic mirroring, I also wanted to see if I could also monitor the health of my Plex media drives so I can take action if one of the drives was having issues.
Since my Plex usage wasn’t great, the amount of idle time on the server would be quite substantial. This go me thinking about also use the server to manage my data files, which were stored on a Western Digital My Book external hard drive, connected via USB 2.0 (my desktop only supports USB 2.0). I figured with the always on option of the server, and the USB 3.0 interface, I could move my data files external hard drive to the server as well.
The added benefit of moving my data files external hard drive to the server is I could also monitor that drive as well to make sure that there are no issues with the drive. Between the data files external hard drive and the Plex media hard drives, the data files external hard drive is more important as it has files I can’t recreate, such as family photos and personal videos.
To better protect my data files, I could add a second external hard drive, and mirror the current data files external to the new drive. I could also transfer my Backblaze account to the server from my desktop so my data files can always be backed up since the server is always on.
I will continue to edit my photos on my desktop, but I will set up shares on the server that will allow me to map to the photos from the desktop for editing. This will also provide more protection for my data files from such threats as ransomware or other malware that can cause me to lose my database. I will talk more about how I handle this in another post.
With all my ideas for my new server, it was time for me to put it into action.
The Plex Media Server Setup
To help understand what I would like with my Plex Media Server, here is a quick summary:
- My Plex media files on my Western Digital Duo external drives to be mirrored automatically.
- My personal data files on my Western Digital My Book external drive to be mirrored to a second external hard drive.
- My personal data files to be automatically backed up to Backblaze.
- All hard drives in my server to me monitored to make sure there are no issues.
The good news is that all the above points can be managed with very little hardware, software, and with minimal setup. To accomplish my goal, I would need the following:
- Western Digital Duo 8TB
- This as an external enclosure that has two 4TB Western Digital Red drives. I bought this about a year ago to store my Plex media files, and I just needed to connect it to my server.
- Western Digital My Book 3TB
- I bought this drive when the 2TB Western Digital external drive that contain my data files showed signs of failing – bad sectors. That drive was over 5 years old, so it was time to replace the drive with a newer model.
- Western Digital My Book 3TB #2
- This external drive I had just bought a few days ago so I could create a mirror of the first 3TB external hard drive – the drive that has my data files.
- Stablebit DrivePool
- This is the software that is going to duplicate both my Plex media files and my data files to the correct drives automatically. Stablebit DrivePool easily combines the disk space from both external hard drives into a single drive.
- Stablebit Scanner
- Software that will easily allow me to monitor all my hard drives, and integrates effortlessly with DrivePool. Stablebit Scanner will also notify me, via email, if there are any issues with a hard drive.
- Backblaze
- My unlimited online cloud backup solution. This software runs as a service and will continuously monitor my data files for changes and then automatically upload the changes to the Backblaze cloud service.
Before getting into the details of how it all will come together, let me show you how it will be setup with a diagram:
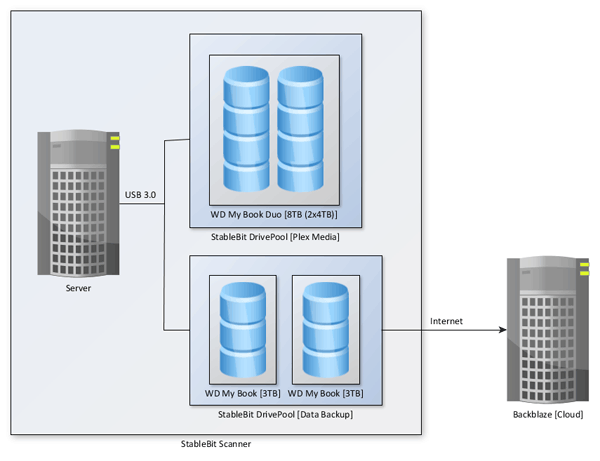
The Plex Media Setup
The main reason I setup the server was to host and stream my Plex media files, so I will start with the Plex media storage idea of the server. The diagram below shows what is involved with setting up my Plex media on my server.
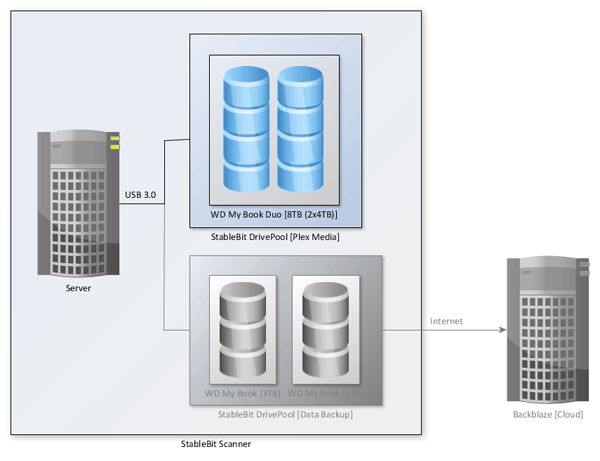
All my Plex media files are stored on my Western Digital Duo external device. This device is considered a DAS (direct-attached storage), because it connects directly to my server through a USB 3.0 port instead of over the network. The device includes two Western Digital Red drives (4TB each), which I setup as JBOD (Just a Bunch of Disks). Setting up the drives in this way allows me to manage the storage setup of the disks using DrivePool
I create a single drive pool for my Plex media files from within DrivePool and added both hard drives from the DAS to the pool. This produced a pool of 8TB in storage size. After the pool was created, I enabled duplication in DrivePool so that each file stored on one of the drives would be automatically copied to the other drive. This essentially halves the amount of storage space in the pool because each file is stored twice.
If one of the two hard drives in my DAS was to fail, I wouldn’t lose all of my media since all files are duplicated on the other drive. It is, of course, possible for both drives to fail at the same time since they share the same DAS unit, and in such a situation I would rebuild my media libraries. I don’t consider my Blu-ray, DVD, and CD libraries to be critical enough to have a full backup solution as I do my personal data files.
The Data Files Setup
The most important data I have has always been stored on an external hard drive, but it was connected to my desktop . I would turn off the external hard drive when I didn’t need to get access to my data, but it would sometime annoy my wife because she couldn’t easily access digital photos. To make life easier for me, and her, I decided to connect the external hard drive that has my personal data files to the server so it can be accessed at any time.
The diagram below shows how my data files are connected to the Plex server.
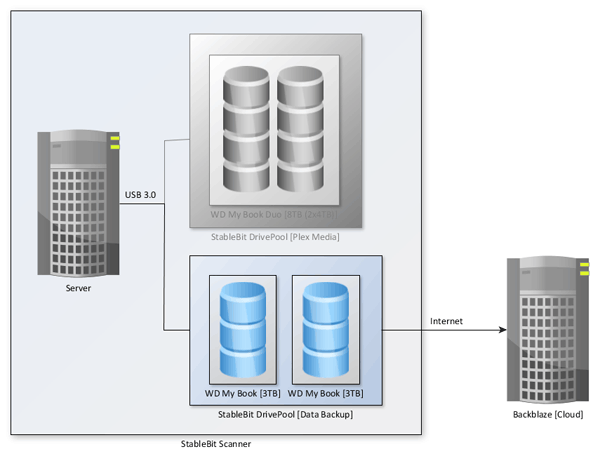
After seeing how easy it was to set up and manage a drive pool for my Plex media files, I figured it would be a great option for my personal data files. I have always made multiple copies of those files, but having multiple local copies was something that I didn’t have. I purchased a second Western Digital external hard drive to contain the copies of my data files.
My data files setup is very similar to my Plex media files, with the exception of using two external hard drives instead of a single DAS device. I create a second drive pool (the first being my Plex media), and then added the two external hard drives to the pool. Because the second external drive was new, and didn’t contain any of my data files, DrivePool took some time to copy over the files from the first drive onto the second drive after I setup file duplication.
In addition to the two local copies, I also have an offsite, cloud copy of my files stored with Backblaze. I have had this setup on my desktop for many years, and I wanted to transfer it to my server so my data files can continue to be backed up online.
I followed the instructions on the Backblaze website about moving my account information to the server, changed the drive in the software to point to the new DrivePool drive and then Backblaze went to work verifying that all files were backed up. After Backblaze quickly went through the list of files in the drive pool, it indicated that all files were backed up and everything was good again.
The result of the above setup is that when I add or change a data file in the drive pool, the file will automatically be duplicated to the second hard drive by DrivePool and then automatically be backed up to the cloud by Backblaze. This means two copies of the file are automatically created without any work outside of adding or modifying the original file.
Monitoring the Hard Drives
The one aspect of managing my data that I had neglected in the past is to actively monitor the hard drives where my data was stored. When I setup my Plex Media server, I wanted to make sure that I also enabled monitoring so I can be more proactive of replacing hard drives that were about to fail. I was lucky with my previous external hard drive as it had just begun to fail and I was able to copy off all of my data. I didn’t want to take the chance again.
For monitoring I installed another Stablebit application called Drive Scanner.
Once I installed Drive Scanner on my server it immediately detected all the hard drives – both internal and external – that were connected to my server. The application began reading the S.M.A.R.T data for each drive and alerting me if there were any issues.
Note:
The S.M.A.R.T. data from my Western Digital external hard drives (not my Western Digital Duo) could not be read and reported by the Drive Scanner application. I had to change the partition of the external hard drives from MBR to GPT for Drive Scanner to read and report the S.M.A.R.T. data from the two external hard drives.
The most common issue I have at the moment is the drive temperatures getting high because of all the copying, especially my data files drive when DrivePool was duplicating the data from one drive to another. When any issue happens, I receive an email from Drive Scanner that describes the issue.
While duplicating files with DrivePool can cause the Drive Scanner to issue heat warnings, the best part of the two applications is that DrivePool will start to throttle the duplication process to help reduce the heat. The two applications work together to make sure that your drives are running without any issue. The integration between the applications is seamless and only requires both to be installed on the same system.
In addition to the S.M.A.R.T. monitoring, Drive Scanner will also check the disks for any issues. The disk scan is set on a monthly schedule and you can see the results directly in Drive Scanner. If needed, I can also start the scan manually. If a drive once again reaches a heat warning, the scanning process will throttle in an attempt to reduce the heat. I usually only scan my drives overnight when there is very little IO on the drives.
My Plex Media and Backup Server
By utilizing my Western Digital Duo, two external hard drives, Stablebit DrivePool, Stablebit Drive Scanner, and Backblaze, I now have a server that can stream all my media to any device I own, as well as automatically duplicate my personal data files locally and offsite in the cloud.
The best part is that this server is running headless (no monitor), and without any user logged in so even if Windows does reboot, such as after an update, I don’t have to remember to go and log in as everything will automatically run without any problems.














 Today, it is hard to imagine day-to-day life without Internet and computers. More and more people are using digital storage units to keep their valuable information and also share it across online communities. The vastness of the digital world and the multitude of networks that are integral parts of the Internet make security one of the top concerns for both users and network managers.
Today, it is hard to imagine day-to-day life without Internet and computers. More and more people are using digital storage units to keep their valuable information and also share it across online communities. The vastness of the digital world and the multitude of networks that are integral parts of the Internet make security one of the top concerns for both users and network managers.