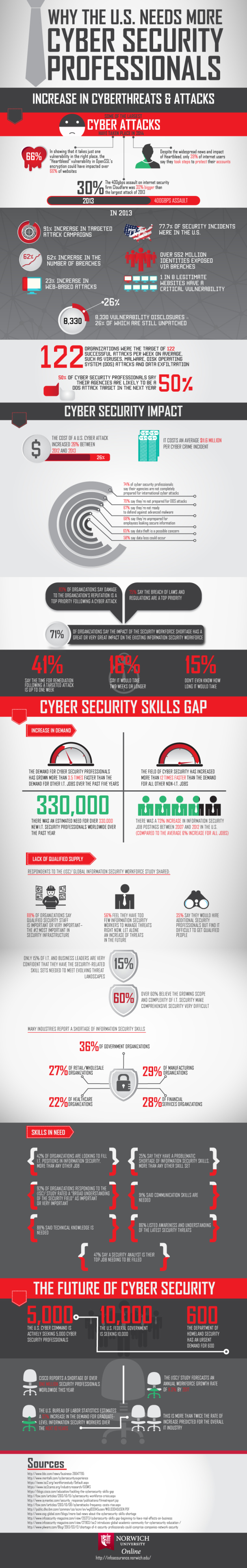
Many people do not realize that some of the largest cyber attacks in the history of the internet took place in 2014. There has never been a greater need for cyber professionals, especially when the security of business and government locations is on the line. Some of the statistics surrounding these attacks are terrifying to think about, and illustrate the need for properly trained professionals all the further.
Increases in Threats
All it takes is one well placed cyber attack to affect everyone. The Heartbleed vulnerability in most OpenSSL encryption could have affected upwards of two-thirds of all websites. Despite how widespread this news was, only forty percent of all users took steps to protect themselves. There has been a ninety-one percent increase in targeted attack campaigns, a sixty-two percent increase in the number of successful breaches, and a twenty-three percent increase in web-based attacks. Almost one in every eight websites has a critical vulnerability.
Cyber Security Impact
The cost to recover from a cyber attack has increased twenty-six percent between 2012 and 2013. The current recovery average is eleven and a half million per cyber crime incident. Over seventy-four percent of all cyber security professionals say that their agencies are not ready for an attack, with many other companies admitting the same faults. Over fifty-eight percent of these agencies admitted that some type of data loss would occur.
Skill Gaps in Cyber Security
The demand for cyber professionals has increased over three and a half times faster than the demand for most other IT jobs in the past five years. Over three hundred and thirty thousand positions had opened up out of necessity for these professionals in keeping a variety of industries safe from cyber attacks. The overall field of cyber security has increased in demand over twelve percent faster than all other types of non IT jobs. A variety of industries report a shortage of such professionals, including the healthcare sector and different manufacturing organizations.
The Future of Cyber Security
Currently, five thousand cyber security professionals are needed in the United States alone, while the federal government is actively seeking over ten thousand. The Department of Homeland Security itself is actively seeking six hundred such professionals to suit their needs. Studies estimate that there will be an upwards of thirty-seven percent increase in the amount of cyber security graduates in the next ten years. Norwich University’s online master of information assurance program put together a detailed visualization of this growing need in information security. Discover more in the infographic below.