The open source community scored a major victory this year as the Android OS took the dominant position in mobile market share, easily beating Microsoft’s closed-source mobile phone platform. ZDNet reports that the Android climbed to 75 percent market share in the first quarter of 2013, after enjoying explosive growth. Even though this isn’t a Linux platform, it is very encouraging news for all open-source fans. It is an especially promising sign for the upcoming Ubuntu operating system for smartphones. Gearburn reports that Canonical Ltd. CEO and founder Mark Shuttleworth has announced that this new OS will begin shipping in October.
Blog
-

Does Your Camera Matter When Taking Photographs?
One of the great debates online regarding photography is how much a photograph is dependent on the camera. As with any debate there are two groups: those that think a great photograph is independent on the camera, and those that think a photograph can be better with a better camera.
To me, a great photograph is not one that is taken by a great camera, but one that is taken by a great photographer.
The Photograph Takes the Photograph, Not the Camera
While I would like to have the latest and greatest in photography gear, I also realize that unless I have an eye for photography, my photographs will just be average, even with the best gear. What separates an average photographer from a great photographer is how they see the world around them.
An great photographer can take a much-talked about photograph not because of his camera, but because of what he sees. While we live in a world where photographers have access to gear that have fast autofocus, tack-sharp lenses, tremendous white balance options, and unlimited post-processing potential, many photographers realize that what they see is the most important part of photograph.
To put this in perspective, all the best known photographs over the past one hundred years were taken by photographers that used cameras that have no where near the technology of the cameras used today. Those photographers used their skill as a photographer to capture what they saw. Even with the best equipment, the average photographer probably couldn’t match what the great photographers of the past produced.
Of course, as with anything in life, having the best camera equipment you can afford can make your life easier – as long as you know how to properly use the camera. For example, a Canon 5D Mk III with a EF 24-70mm f/2.8 II lens and Speedlite 600EX-RT flash will probably make it easier to take a photograph indoors than a Canon PowerShot S110. However, one thing to keep in mind is that making life easier doesn’t equate to better photographs.
But if you provide an experienced photographer with the PowerShot S110, and an amateur with a the 5D Mk III, the experienced photographer will probably still take better photographs with the lower-end camera because they will be more creative when taking photographs. Years of experience will show with every photo they take regardless of the camera. While the amateur has the best of the two cameras, their photographs will probably turn out average.

Niagara Falls Sky Wheel
Canon PowerShot SD1100 IS f/2.8 @ 1/60 sec. ISO 250While many photographers may try to ensure their photos don’t clip the highlights or shadows, the one thing I notice is that the average person doesn’t care about such things. All they care about is what their photographs look like when they receive them, not what the histogram from the photo looks like. If they like the composition and creativity, then the customer will probably be happy. The composition and creativity doesn’t come from the camera, but from the photographer.
While any photographer would always like to have the latest and greatest in gear, the best photographers know that the best gear cannot replace the artistic creativity of the photographer.
-
![Kids Apps: Why Parents Should Be Concerned About App Security [Infographic]](https://technicallyeasy.net/wp-content/uploads/2013/06/children-app-security-200x200.png)
Kids Apps: Why Parents Should Be Concerned About App Security [Infographic]
With the incredible fast adoption of mobile technology in all spaces of everyday life such as in work, home, recreation, and education, it comes as no surprise that mobile usage is on a steep rise among children and young adults as well. Back when there were only cell phones, it was understandable for parents to be able to withhold giving their children access to a personal mobile device for quite some time with the exception of emergency purposes.
But now that we are somewhat of digital technology age, where in order to be a successful and competitive member of society and in the workplace you have to be knowledgeable of all things mobile and internet, parents don’t really have the option of sheltering their children from the internet – they need to know about it or else they suffer as they grow into adults. However, it is still alarming to realize that children in kindergarten and and even younger are already using mobile apps as frequently as most adults.
Meanwhile, many of the apps they use probably don’t have proper security measures for child-use. This infographic, “Kids Apps – Why Parents Should Be Concerned About App Security,” gives a great overview of the statistics of child mobile app usage, vital stats of mobile app development, how these apps can find and use your personal information, how these apps might allow your children to spend money without permission, and most importantly, the things you need to know to protect your information and your children. Find out more below.

This infographic is by Veracode, an award-winning application security company specializing in secure software supply chain and other security breaches with effective risk assessment tools.
-

FAQ: Securing Your Wireless Network
Ever since I have been writing posts about securing home wireless routers, I have been asked many questions about such security. Many of the questions were the same, such as what happens if you forget your router’s password, while others have been about how best to secure a wireless router.
Since I have received quite a few questions over the years, I decided to gather the questions in a post and then add my answers to those questions. Of course, if you have additional questions you can continue to send them to me, or write them in the comments section of this post.
-

Warning: You’re Spending Way Too Much on That Pre-Built Gaming Computer
In the modern gaming world, no platform is as rich or as rewarding as is PC gaming. Gaming on the PC offers better graphics, superior multi-player options, better gameplay, and overall a better gaming experience. However, one reason why most gamers are still playing on a console is that they believe the cost of getting a computer good enough to play the top games is way too high. And, rightly so…
If you look at the cost of the “high-end” gaming computers that some manufactures are producing, it’s obvious why more gamers aren’t switching to the PC. They’re too damn expensive.
For just a smidge over $3,000 you can get a pre-built computer that promises to play any game on the highest settings. It’s not reasonable at all, but people pay those prices. Unfortunately for them, they could’ve saved themselves thousands of dollars if instead of buying their computer pre-built, they instead bought the components and built it themselves…
-
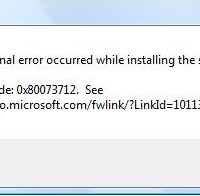
How to Fix Windows Update Error 0x80073712 Or 80073712
One important aspect of using Windows is to keep it updated at all times. Microsoft releases security fixes on the second Tuesday of every month, so it is important to ensure you install those security updates to keep your system safe.
Of course, as with anything software, you may encounter errors from time-to-time that prevent you from installing updates. There are many different errors you can receive, but this post will explain what you can do if you get a 0x80073712 or 80073712 error when updating Windows.
-

Why Your Wireless Network May Not Be As Secure As You Think
I have written several posts on securing a wireless router. I have even written posts that provide step-by-step detail on how to secure specific models of wireless routers. While you should enable WPA2 and use a strong passphrase, that may not be enough to keep your wireless network protected by unauthorized users.
In many routers manufactured today, there is a known issue related to a technology that has been pushed by the wireless industry to make setting up and securing a wireless network easier. Unfortunately, this new technology has also opened up a large security hole that can allow unauthorized users access to your wireless network – even if you secured your network with WP2 and a strong passphrase.
WPS – WiFi Protected Setup
When wireless networks started to become popular, many people weren’t aware of the security that needed to be implemented in order to protect their network. Most people were just used to use standard network routers where you just plugged in a computer using a network cable and everything was good to go.
Unfortunately, with wireless, security is vital. Anyone with a wireless network card that is within range of your wireless router can connect to your network. The problem is that many people don’t understand how to properly secure a wireless router. Let’s face it, many people don’t want to navigate through an array of confusing options and try to understand terms like WPA, WPA2, AES, TKIP, etc.
In 2007, the WiFi Alliance created WiFi Protected Setup (WPS) that provides an easy way for someone to configure and setup security on a wireless network. The way WPS works is a wireless router is shipped with a personal identification number (PIN) – usually 8 digits in length – that is printed on a sticker on the router. With WPS, a user can then enable encryption for the wireless network by pressing a button on the router and then entering the PIN in the network’s setup wizard.
While this sounds like a great way of connecting devices to a wireless network easily, there is one issue: is can easily be hacked. WPS was created with usability in mind and not security.
In December 2011 researcher Stefan Viehböck reported a flaw that showed brute-force attach feasible against WPS. This flaw allows unauthorized users to gain access to a wireless network.
While the PIN is an 8 digit number, the last digit is a checksum of the first 7 digits, which leaves 107 = 10,000,000 possible PIN numbers. The issue is that the router will confirm validity of the first half (4 digits = 10,000 possibilities) and the second half (3 digits = 1,000 possiblities) separately, which reduces the number of possibilities to guess to about 11,000. Since WPS doesn’t lockout after several incorrect attempts, it wouldn’t take long for a device to guess the correct PIN and gain access to the wireless network..
Protecting Your Network
The issue with WPS is that many routers may have it enabled by default – even if you have used the feature or not. This makes your wireless network vulnerable to a brute-force attack.
The only solution, at the moment, is to disable WPS from within the router’s administrative dashboard. Some routers provide an option to disable WPS, while others require a firmware update. My Linksys E4200 required a firmware update to disable WPS.
If you are unsure of whether your router provides the ability to disable WPS, you should ask the manufacturer, or use their support forums and ask other owners. You may have to update the firmware on your router, as I had to do.
While WPS provides an easy way to attach devices to your wireless network, the lack of security in such a feature, in my opinion, far outweighs the usability. I suggest you manually attach devices to your network, once the network is secured, and turn off WPS instead.

