In September 2013 a new type of malware was discovered to be making the rounds in computers running Microsoft Windows. This new malware is not really a virus because it typically requires a user to open an infected e-mail. What makes this malware particularly dangerous is what it does once it infects your computer – it holds your files for ransom.
This may sound funny at first, but this type of malware – called ransomware – is very serious. The malware that was recently discovered is called CryptoLocker, and has begun causing pain for many users around the world.
Money for Your Data
In case you haven’t heard about ransomware, it is malware that infects your computer and then restricts access to your computer. Once the restrictions are in place, the malware will then request a ransom to remove the restrictions. If the ransom is paid, the restrictions are removed.
With CryptoLocker, the restrict is access to your data files. When CryptoLocker infects your computer it will then silently begin encrypting your local data files without you even knowing your files are being encrypted. While you may have an anti-virus product installed, it may not detect CryptoLocker, or it may detect the malware once files have been encrypted.
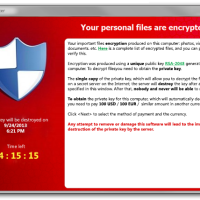
When CryptoLocker encrypts files on your computer, it uses what is called a public key, which it obtains by connecting to a command-and-control server online. In order to decrypt the data, a private key is needed, which is stored on a command-and-control server. The private key is, therefore, never stored locally, so you can’t decrypt the data yourself. Decrypting the data yourself is impossible without the private key.
Once your data is encrypted, you are presented with a message to send a specified amount of money to remove the encryption. The amount of money is about $100 USD or $300 USD. The payment is to be made through MoneyPak, Ukash, cashU or Bitcoin. After a specific time without payment, the key that is used to decrypt your data is destroyed and your data can’t be decrypted.
What files does CryptoLocker encrypt? Files with these extensions 3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, ????????.jpg, ????????.jpe, img_*.jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odc, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pdf, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, sr2, srf, srw, tif, wb2, wpd, wps, x3f, xlk, xls, xlsb, xlsm, and xlsx. This is a long list is contains most common data files that everyone uses.
Not only can the data files on your local, internal hard drive be encrypted, but it has also been reported that files on attached external hard drives and network drives can also be encrypted.
Protecting Yourself From CryptoLocker
The best defense, as it is with most malware, is to ensure you don’t open strange e-mail messages. With CryptoLocker, it is send through well-crafted e-mail messages.
The e-mail messages may inform you about a customer support-related issue, or perhaps a message from a courier company, such as Fedex, UPS, etc. The e-mail messages will include a ZIP attachment that contains the CryptoLocker program. The program itself is disguised as a PDF File – including the PDF icon – but has a name like FORM_101513.pdf.exe.
As I mentioned above, if you don’t recognize the e-mail, or it doesn’t make any sense to you, just delete the e-mail without opening it.
Also, you should ensure that you always backup your data. I recommend you use Backblaze (I use them) to backup your files. If CyrptoLocker, or other malware, destroys your files, then you can always restore them with Backblaze.