VPN stands for virtual private network. This is often used as an application which lets the computer or other device access information from wider sources. A VPN also lets the user access information from sites which have been blocked by certain servers at a national level. However, when using a VPN, the information that is transferred between you and the Web server is completely secure. A person can get filtered and safe information from the use of this VPN.
Category: Security
Security is an important topic when it comes to technology. There are many different areas of security, so this category is divided into various sub-categories to help navigate through the posts on security.
-

Establish a Positive Online Presence
Real life is about to begin. You are out of the house and off to college. If you are lucky, you have a laptop to take to college with you. This laptop is a gift, but it can also be a curse if you don’t know how to use it correctly. Laptops are convenient, for sure, but they are also prime targets for hackers and thieves who want to get a hand on your personal information. Prevent your private information from leaking online.
-
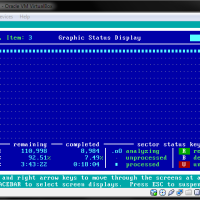
How to Run SpinRite in VirtualBox
SpinRite is a popular hard drive maintenance and data recovery software from Gibson Research Corporation, and costs $90 to own. While I haven’t extensively used the software, it has helped me recover data from hard drives when I thought the data was lost. It is a small application, and you also don’t need a powerful PC to use the application.
The once aspect of SpinRite that makes it different from other drive maintenance and data recovery tools is that you are required to boot up your computer using SpinRite to launch the application. SpinRite loads a copy of FreeDOS, detects the disks on your system and then allows you to perform specific scans of the disks.
Of course, if you need to scan a hard drive, you will usually need to connect it to either the IDE your SATA interface within your computer, which requires you to open up computer, and then connect the hard drive to the correct interface so the FreeDOS operating system can find your hard drive. In order for you to connect the drive to the USB port of you computer requires you to load the USB drivers within FreeDOS in order for the hard drive to be detected.
The alternative is to use a virtual system created by software such as VirtualBox to automatically setup and use a hard drive that is connected to a USB port. While the scanning may not be quite a fast, it is much easier to simply connect a hard drive to a USB port and then have SpinRite scan the hard drive in a virtual system.
I outline the steps that you need to follow to run SpinRite in VirtualBox.
-

Is Your Computer Ready for Cyber Attacks?
Small businesses and private individuals should step up their computer security today. Statistics reveal that cyber criminals are attacking those two factions more intently now. Fortunately, reinforcing your line of security is not as hard as you think.
Small businesses and private individuals are both prone to thinking that they are the last in any cyber criminals’ hit list. With so many large corporations around the world, there’s little chance that any smart criminal will waste his time on you. The one thing you got right in that mindset is that those criminals are indeed very smart, and because they are, they understand that the small things are what make up the big things…and that is you.
-

Top 4 Cloud Storage Providers
Anyone who is willing to protect their files, as well as, data from any type of computer hardware or software crash really needs to sign up with a cloud storage provider. This is mainly because of the fact that with a small amount of files, one can get an absolute backup of each and every file they want.
In the following post you will get to know about the top 4 cloud storage providers for you to go with:
-

3 New Identified Trends In Home Security Tech
While many of you would be aware of the importance of home security systems, it can get overwhelming if you’re still yet to purchase a unit for your home. Previously, the systems were merely considered as getaway parts, but there have been a lot of advancements in recent times such as wireless networking and integration of mobile apps which have enabled the systems to perform multiple functions at the same time.
According to a survey conducted by Consumers Reports National Research Center, 80% homeowners are satisfied with their security systems when it comes to effective protection of their homes. However, Angie Hicks, who collects ratings from customers on different categories on Angie’s List, revealed that home security alarms is one of the categories consumers complain about and also mentioned that some security companies insist on signing monitoring contracts over the long term.
-

Java – A Huge Security Problem in Your Computer
Many of the attacks on a computer system involves exploiting weaknesses in installed software. Everything from the operating system, Web browsers, office software, and software that just connects to the Internet, may have weaknesses that hackers can exploit to install malicious software. Most of the time malicious software that targets a particular application exploit is limited to a particular type of computer, such as Windows or Apple. This is why it is always important to ensure you keep the applications installed on your computer updated with the latest patches.
There is one piece of software that is exploited on a regular basis, and the exploits aren’t limited to a particular system. This software is designed to work on many different systems, so it is an extremely easy target for hackers. The software is Java.
-

FAQ: Securing Your Wireless Network
Ever since I have been writing posts about securing home wireless routers, I have been asked many questions about such security. Many of the questions were the same, such as what happens if you forget your router’s password, while others have been about how best to secure a wireless router.
Since I have received quite a few questions over the years, I decided to gather the questions in a post and then add my answers to those questions. Of course, if you have additional questions you can continue to send them to me, or write them in the comments section of this post.
