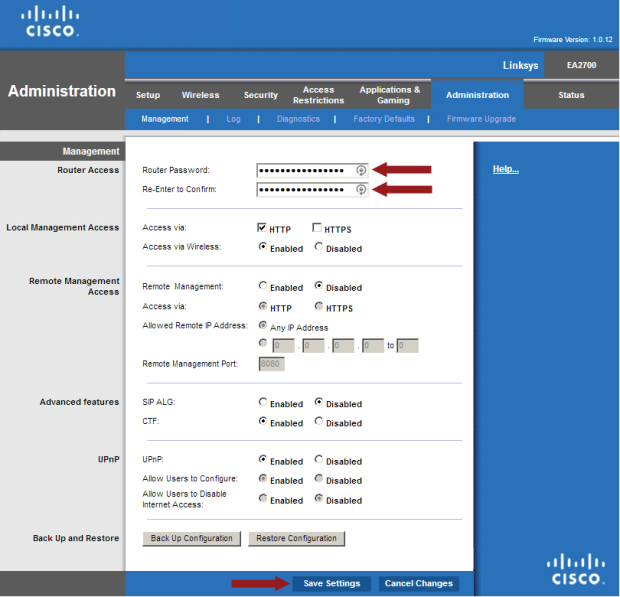
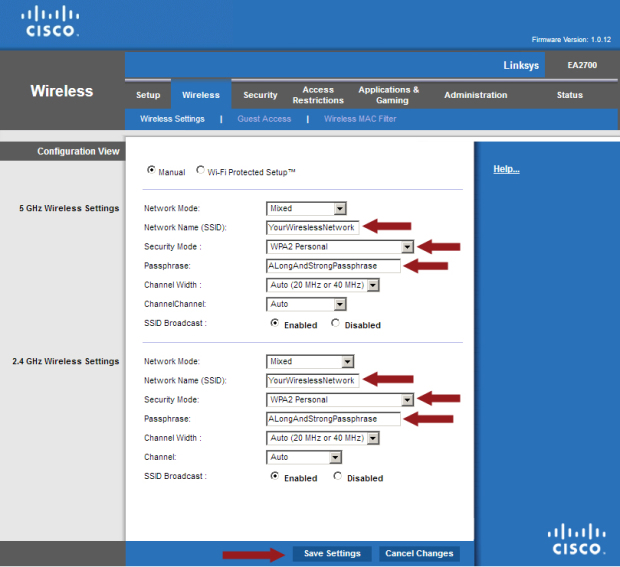
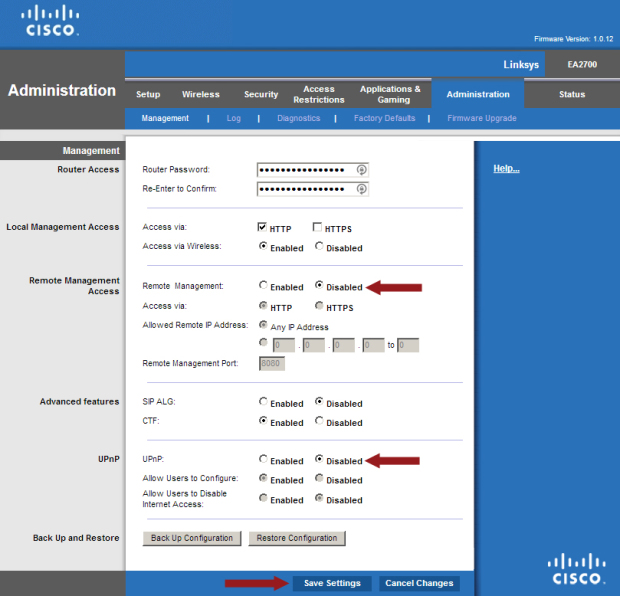
There may come a time when, without tether to logic or reason, you may begin to think that the number of DDoS attacks can no longer rise because there is no more room on the internet.
That the DDoS attacks that have already occurred have taken up all the space that could possibly be allotted to such damaging cyber assaults and any new attempts will simply have to be turned away.
However, websites and businesses across the internet should probably be aware that if it didn’t happen in Q3 2017, it probably isn’t going to. DDoS attacks have hit a major uptick, and even worse? They’re getting more sophisticated.
By the numbers
The good news is that from the second quarter of 2017 to the third quarter of 2017, monthly distributed denial of service (DDoS) attacks only rose 35%.
If you’re thinking that doesn’t sound like good news, well, it will after this next stat: from the first quarter of 2017 to the third quarter of 2017, monthly DDoS attacks rose 91%. Ninety-one percent. Just 9% less than a full 100%. In less than a year.
That Q3 rate basically translates to eight attack attempts per day per organization for a total of about 237 attempts per month. Yes, that number is still per organization.
Two-hundred and thirty-seven attempts to make an organization’s website inaccessible to its users and customers, leading to frustration and a long-term loss of loyalty from which it can be impossible to fully recover.
Placing the blame
The biggest cause of this increase is easy to point to, literally. Look around the room you’re in and point at the DVR, webcam, router, or any number of Internet of Things (IoT) devices.
These so-called smart devices aren’t terribly brilliant when it comes to security as they’re generally designed with more of an emphasis on innovation than safeguarding against malware.
Compounding those issues is the fact that users don’t often think to change the default admin names and passwords, and if they do think to, it often isn’t easy to accomplish.
These factors combine to great billions of bullseye devices in the IoT for hackers creating DDoS botnets by infecting devices with malware that allows them to be controlled remotely.
It’s now easier than ever to assemble botnets of a significant size, and since a DDoS attack is a distributed form of a DoS attack, the more infected devices at an attacker’s disposal, the more damage he or she can easily do.
For many enterprising cybercriminals, that damage is done thanks to DDoS for hire services, another major factor in the increase of incidents.
Anyone with an internet connection, a bit of money to spare and the willingness to commit a cybercrime can pay as little as a few dollars to rent the use of a botnet and launch a DDoS attack at any website they’d like.
Whether users are signing on to settle grudges, cause random chaos, enjoy the fallout on social media, or even send a DDoS ransom note demanding payment in exchange for no further attacks, this is a business that’s booming.
Yet another issue
While on the one hand, the ease of building a botnet and getting to use one has certainly hugely contributed to the current distributed denial of service epidemic, on the other hand there is an increase in complexity that’s also causing problems.
Typically, the attacks that come from DDoS for hire services are short-burst and relatively low-volume. The for-hire attacks that aren’t, are massive volumetric bruisers coming from IoT botnets, the ones that grab headlines for their firepower.
Generally speaking, the more a user is willing to pay, the bigger and longer the attack. These attacks don’t account for the entire increase in monthly assaults, though: in the second quarter a full 20% of attacks were multi-vector, which are sophisticated attacks that use at least two different methods to try and beat site security and get attack traffic to the victim server.
Worse yet, these sophisticated attacks – undertaken by skilled attackers as opposed to the average spiteful internet user – are often accompanied by malware or used as a distraction for another data extraction attempt, making the potential consequences of a successful DDoS attack even more dire than they already are.
Piling on
DDoS is not a new threat. Security experts and even many non-experts have been harping on the risks of failing to adequately protect against these attacks for years.
It’s at the point now where, for reasons that vary widely, nearly every website is at risk of a serious attack and in need of professional DDoS mitigation services.
The odds that DDoS attack numbers will go from a 91% increase over the course of three quarters in 2017 to falling in 2018 are not good, to put it mildly.
Nor are the odds that attackers will cease assembling those easy IoT botnets and making bank on for-hire services, or launching sophisticated attacks that can worm their way through security defenses and possibly even result in data breaches.
Further, the odds are truly terrible that the internet will reach a DDoS attack limit, no matter how sharply numbers keep increasing.