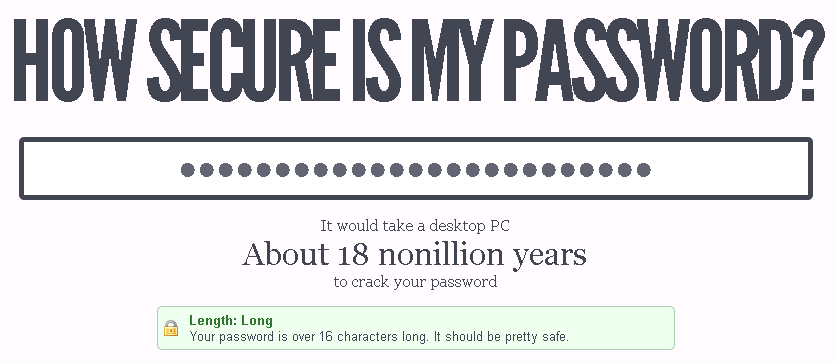It was reported and confirmed yesterday about 6.5 million LinkedIn accounts compromised with the the hashed passwords to those accounts uploaded to a Russian hacker forum. Unfortunately, events such as these are all too common each year, which causes personal information and identities to be stolen as a result.
While you may not be able to prevent security breaches, there is still one thing that you can do to make it hard for others to gain access to your personal accounts.
Password Hashing
A common way for companies to store your password is by create a hash of the password and then storing the hash. For those that don’t know, a hash is a cryptographic function that will take an arbitrary block of data and create a fixed-length string of that data.
Hashes are a one-way operation. This means that you can’t take a hash and create the original string from that hash without a brute-force method. Any size data can be hashed, from one character to billions of characters. The data you hash will always produce the same hash value.
There are many different hash algorithms in use today, with some algorithms being more secure than others. In the case of LinkedIn, it is reported that they used the SHA-1 hashing algorithm to hash the passwords and store them in their system. While the SHA-1 hashing algorithm is a very secure algorithm, there are still reasons why passwords were known after the compromise.
Adding Salt
To help make the hash more secure, a method involving adding a salt value is used. Much liek you would add salt to food to enhance the flavour, a salt is used to enhance the security of a hash value.
When a value, in this case a password, is hashed a random number of characters, called a salt, are appended to the password to increase the length of the password, and therefore, increase the difficulty of guessing the password. The password and salt value is then use together to create the password hash.
For example, a common password used is “Password1”, and appears in many password lists. It is easy to determine the hash value of this password, so the hash is known. But when a salt value of “#246imANRGX9kNzx” is added to “Password1”, the new hash will be generated from “Password1#246imANRGX9kNzx”, which will create a different result than the “Password1” hash. Not only has the hash changed, but the length of the password has changed, as well. The length of the password is important for password strength.
Unfortunately, it has been mentioned that LinkedIn didn’t include a salt with their passwords, which means just the password was hashed. While a salt is extremely important with regards to security, there is still another option to implement to ensure your passwords are as secure as they can be – from a user’s perspective.
Creating Hard-To-Guess Passwords
I see a list of the most common passwords in use on a regular basis. It doesn’t surprise then when a list of passwords from a compromised site that many of the most widely known passwords are usually on the comprised site’s list.
Regardless of whether the passwords are stored in plain text, encrypted, or hashed (without a salt), if you use a well known, easy-to-guess, password, it may only be a matter of time before your account is hacked.
As explained above, a hash is a one-way operation, but the hash for a value is always the same. Many of the common password hashes are well-known so an unsalted hashed password stored in a database is easy to crack.
The best way to protect your accounts is to create long, and complex passwords. Random numbers, letters and symbols (if permitted), make great passwords. How to create a random password, and be able to remember the password? Through the use of a password manager. I use LastPass for generating my passwords and storing them so I can easily access them. There are many reasons why I use LastPass, but password management is the main reason.
While systems are compromised and personal account information is retrieved, using a strong password is very important. While we hope more companies start implementing password hashing with a salt value, we, as consumers don’t have control over that aspect of security. The best we can do is to create long, complex passwords in the hope that are data remains secure.